Think of all the mundane, daily tasks in life — commuting to work, paying bills, grocery shopping, talking on the phone. Each one requires an identity of some sort — a driver’s license, an account number, a phone number. With the advent of technology, this need for an identity transcended into the virtual world and with it; spam signups.
With the internet came countless websites offering a vast number of services to users. This created a need for virtual identities and lead to the creation of the signup and registration process. However, with each website providing its own user registration process, each virtual identity was quickly scattered across the internet.
Each user registration process affects the overall user experience. It can either be a user annoyance or provide seamless access to the services that the website offers and creates a personal user account for each individual. This process establishes the identity of the user on each website.
The signup process is equally important for the website offering the service by creating a database of the users accessing its web properties. The user registration process supplies site owners with important demographic data about their users. With technologies such as big data evolving, companies are using this information to understand user behavior and customize the whole user experience.
What are Spam Signups?
Malice surfaces in the virtual world in many ways. One great example is spamming. Spamming involves flooding an application with dummy data through automated programs. The registration process is just one area of the digital landscape that has been a victim to spamming in the form of spam signups. Bots (pieces of software) are built specially to flood the registration database with irrelevant and dummy data.
The bots are programmed to submit fake registration form information directly to the server by bypassing the website code with help of utilities like ‘curl’ and ‘postman’. Advanced bots interact with the website code and spam without bypassing the code.
Spam Damage
User registration data has many uses. It gives insight into consumer behavior and provides a rich source of information for advertisers and marketing professionals.
When a website falls victim to spam signups, its database is infused with fake data. This skews their data thereby decreasing the credibility of the database. Without accurate data available, these websites have difficulty attracting others to advertise on their site and won’t know for sure who their typical user is.
Websites also use user registration data to tailor their services to customers so skewed data affects their ability to serve the customer. For example, an online clothing retailer may have a larger female consumer base, but due to spam signups, the data is skewed to represent a larger male base. This would affect the site’s inventory and marketing decisions among many others and could cause a loss in revenue and damage to their reputation.
But businesses are not alone. Consumers are also is affected by spam registrations as businesses are unable to deliver personalized services targeted to their true target market when they have incorrect data about their consumer base. This can cause frustration and confusion amongst site users as they fail to be met with the experience they expect.
So is there a fix? Sure, spam data can be deleted. However, cleaning a business’ database system to remove spam data utilizes considerable resources that could be better spent in other areas of business operations. It’s far better to start combating spamming before it affects your site.
Combating Spam Signups
With the damage caused by spamming only increasing, a number of methods have been developed to prevent (or at least reduce) spam signups before they cause database damage.
Lets take a look at 4 popular ways to stop registration spam:
1. CAPTCHA
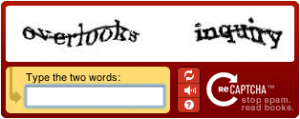 CAPTCHA codes are the most prevalent form of security against spam signups. The main purpose of CAPTCHA code is to differentiate humans from bots. The most widely used CAPTCHA schemes use distorted characters that humans can recognize but that automated scripts have difficulties with.
CAPTCHA codes are the most prevalent form of security against spam signups. The main purpose of CAPTCHA code is to differentiate humans from bots. The most widely used CAPTCHA schemes use distorted characters that humans can recognize but that automated scripts have difficulties with.
 Pattern recognition and audio and visual forms are some of the CAPTCHA codes that are used. Developers have also tried experimenting with the CAPTCHA codes. In the case of Snapchat, it’s verification system asks users to select the image with a ghost in it to prove that the user is human.
Pattern recognition and audio and visual forms are some of the CAPTCHA codes that are used. Developers have also tried experimenting with the CAPTCHA codes. In the case of Snapchat, it’s verification system asks users to select the image with a ghost in it to prove that the user is human.
However, CAPTCHA codes have faced their own set of problems. Most notably, they receive flak from the visually impaired. Also, they are often difficult for users to decipher which causes frustration and increased abandon form rates.
Plus, it’s not a perfect method to stop registration spam as expert spammers have been able to build bots to break through CAPTCHA codes. These DeCAPTCHA techniques are prevalent and are developed for every new CAPTCHA method created. CAPTCHA techniques may help to protect a site against brute force attacks, but are not sophisticated to provide your registration process with all the protection it needs. They’re a good start but you should look into other modes of security as well.
2. Mobile Number Verification
Mobile verification is a prevalent practice especially in the banking sector. This process sends users verification codes on their mobile devices which then need to be inserted back into the registration form field to complete the user registration process.
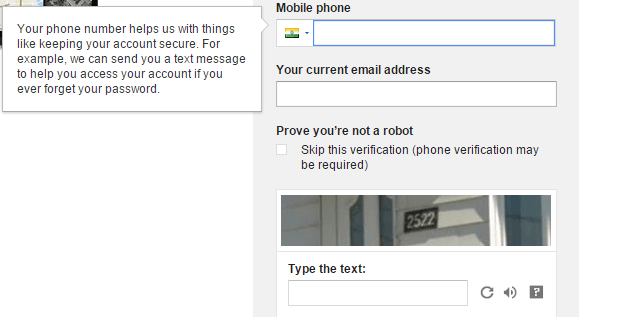
It is an extremely effective method as it requires interaction which only a human can complete. Plus is extremely safe as the code is sent to a mobile device independent of the website. This makes it popular amongst sites very concerned with security such as Google.
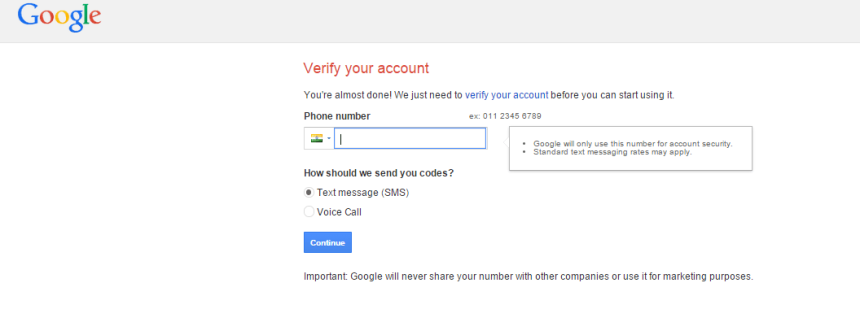
Unfortunately, this mobile verification system relies on all users to have a mobile device and an active mobile network—the process fails if the user is out of their mobile coverage area.
Mobile verification can also greatly extend the signup process with the user having to enter registration information, provide a mobile number, wait for a code, and then re-enter that code into the system. Obviously it scores low on ease of use and may test the patience of the user.
3. Social Login
Social login allows users to sign up on a new site with an existing social account. The process ensures that users do not have to go through the tiring process of filling out registration details and leverages the security of established sites such as Facebook and Google.
It’s pretty tough for bots to have fully established accounts on social networks and then be human enough to use those social accounts to complete spam registrations, so it’s a great way to stop spam signups on any website.
All the user has to do is to log in with their Facebook credentials and their user data is automatically collected from their Facebook account (with their permission of course). This significantly reduces the time, effort and energy of the user while registering and provides a unified online identity through existing social networks.
4. Honey Pot
A ‘honey pot’ is a field added to user registration forms that human users can’t see due to CSS or JavaScript used to hide the field. ‘Honey pots’ are awesome for the user experience side of things because they don’t inconvenience users like CAPTCHA codes, but are still a valid tool for thwarting spam bots. Basically, a spam bot will fill in the ‘honey pot’ field that valid users can’t see, alerting you to their spamming activity. If the ‘honey pot’ field is filled in, you can confidently reject the registration as spam.
‘Honey pots’ are a smarter way of keeping spammers at bay. The important thing to remember is to not alter your external response in any way if the field is filled. Show the same confirmation, thank you page, or whatever messages or pages normally come after registration. That will prevent the bot from knowing it has been flagged as spam.
Unfortunately, ‘honey pots’ do not ensure complete immunity from spam registrations though as spammers are always inventing new ways to get around anti-spam measures. ‘Honey pots’ also require considerable effort to implement in the website code and continuously update and maintain so that spammers are not able to break through them.
Conclusion
The registration process itself is always prone to spam attacks and negatively affects both the users and the website owners. Websites are always looking for new ways to stop spam registrations while spammers quickly adapt to each new tactic but this shouldn’t dissuade you from doing all you can to protect your site from registration spam.
Thoughts? Found another anti-spam technique that has worked for you?
Let me know in the comments!
(366)