Offboarding employees presents serious data security risks. Are you worried about the damage a terminated employee could cause with access to your sensitive corporate information, account passwords, and other proprietary data? Follow these 5 data security tips to protect your sensitive data against insider threats when offboarding.
The Tips at a Glance
- Follow an employee offboarding checklist
- Keep IT personnel informed of upcoming terminations
- Maintain accurate IT inventory
- Monitor employee computer activity
- Deprovision access to accounts & data
What Are the Data Security Risks of Offboarding Employees?
- Data loss through vandalism (file deletion, misconfiguring servers, etc)
- Compliance violations (leaking or destroying protected classes of data)
- Stealing intellectual property and taking it to their new employer
- Stealing sensitive records and selling it for financial gain
The greatest risk is the theft or loss of sensitive corporate data. Disgruntled employees have a higher motivation to steal sensitive data and sell it to competitors or threat actors. The personally identifiable information (PII) of customers can readily fall into the wrong hands following a less than amicable termination.
The risks of data theft are pervasive throughout an organization, particularly for roles with elevated privileges. A survey by security firm Cyber-Ark found that 88% of IT workers would take sensitive data with them if they were fired and 72% of CEOs in a Code42 report admit they’ve taken valuable intellectual property (IP) from a former employer.
A formal offboarding process is critical for protecting sensitive data. An Intermedia study found that 89% of employees were able to access sensitive corporate applications well after their departure. Without a formal deprovisioning process these accounts can be readily abused, leading to a costly data breach. Despite these risks only 29% of organizations have a formal offboarding process.
The Types of Data Most Likely to Be Stolen

The data types that are most likely to be targeted for theft are those with significant financial value. The 2019 Verizon Data Breach Investigations Report found that 71% of data breaches are motivated by money and only 25% of breaches are motivated by espionage or attempts to gain a strategic advantage.
The most valuable categories of data are confidential data such as trade secrets that can be sold to competitors or personal information that can be used for identity theft.
- Passwords (SaaS products, internal accounts, social media, etc)
- Personally identifiable information (PII)
- Non-public financial information
- Intellectual property (IP)
- Customer lists
- Customer data
- Pricing lists
- Emails
Data Security Best Practices for Offboarding Employees
1) Follow an Employee Offboarding Checklist

The offboarding process needs to be thoroughly planned. Following an employee offboarding checklist that is tailored to your company ensures that critical data security steps aren’t forgotten or overlooked.
Mitigating risks during termination includes a mix of administrative and technical considerations. When determining the steps that will be included in your offboarding checklist, involve relevant stakeholders from HR, IT, and management to ensure that each component is addressed.
Examples of Offboarding Items
- Immediately disabling Active Directory account and deleting it after 30 days
- Reviewing the organization’s data security policies with the employee, reminding them of the types of data that they are not permitted to take
- Revoke access to corporate accounts including cloud services, emails, and remote access credentials
- Disabling their accounts and changing passwords on any shared accounts
- Conducting an exit interview
2) Keep IT Personnel Informed of Upcoming Terminations

Human resources, direct managers, and IT need to work cooperatively to protect data during termination procedures. Providing IT personnel with advanced notice ensures that they are ready to immediately deprovision access to corporate accounts and monitor employee computer activity for suspicious behavior leading up to the day of the termination.
When the time is appropriate, you should also notify current staff members of the termination. This will not only help prevent rumors, it will ensure that employees do not fall victim to social engineering tactics. Unaware staff may grant the former employee with unauthorized access to company assets.
3) Maintain an Accurate IT Inventory

During the offboarding process you will need to collect all company assets from the employee. Upon departure an accurate inventory will ensure that laptops, computers, USB storage devices, key cards, and other assets are accounted for. This inventory must be consistently maintained so it can be safely relied on to keep track of loaned assets.
4) Monitor Employee Computer Activity
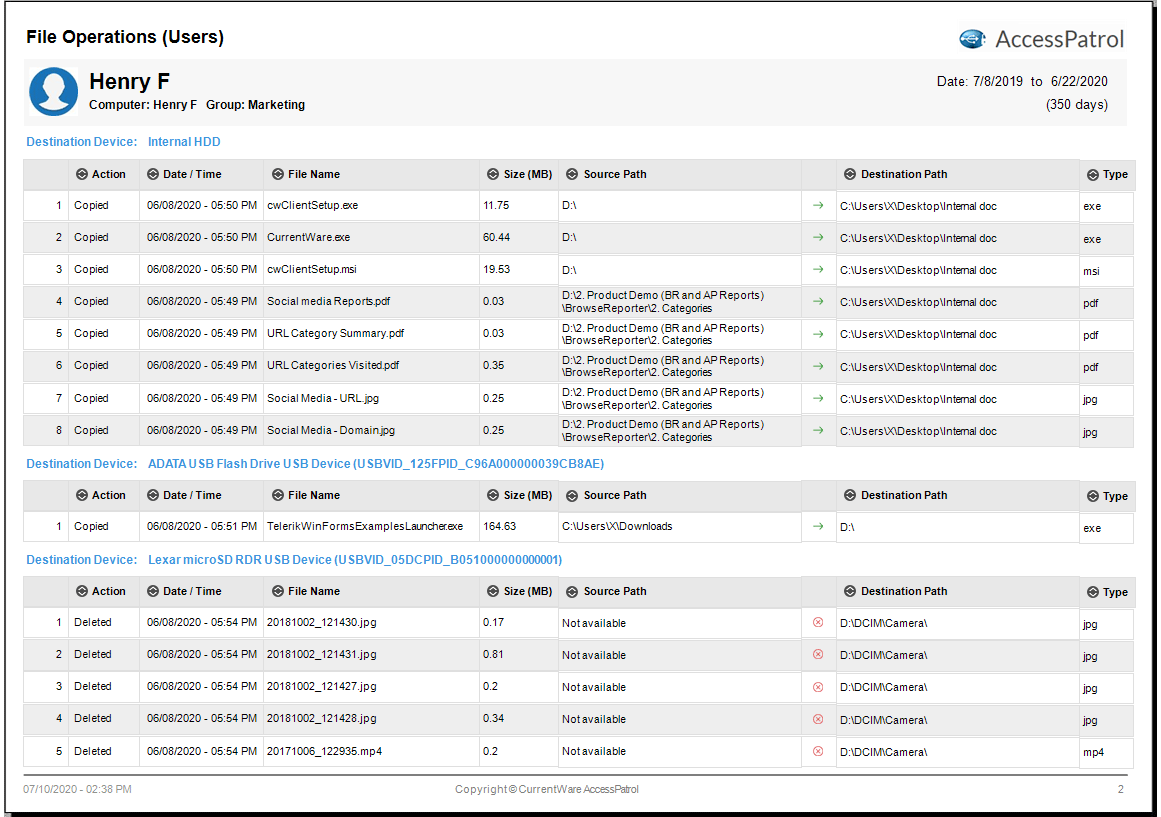
The days leading up to the employee’s departure are an opportune time for data theft and other high-risk behavior. The computer usage of departing employees must be closely monitored for suspicious activity.
- Monitor file transfers to external storage hardware such as USB devices
- Review internet history for visits to unauthorized file storage websites
- Track their application usage for unknown software
- Monitor email activity for sensitive data or attachments being forwarded to personal accounts
- Review logon activity and remote access logs for anomalous behavior such as unknown devices, new locations, or activity after normal working hours
Monitoring the computer activity of departing employees provides an opportunity to detect instances of attempted data theft before the data is breached. This process can be made less resource intensive by configuring context-sensitive alerts in your data loss prevention and employee monitoring programs.
5) Deprovision Access to Accounts & Data

Deprovisioning is an integral step of employee offboarding. While this step can be done manually, automating the process with an Identity and Access Management (IAM) solution will reduce the time it takes to revoke user privileges and ensure that the employee no longer has access to their former accounts.
- Block data transfers to portable storage hardware
- Reset entry codes to the office building
- Deactivate any accounts associated with the employee
- Update the passwords for shared accounts
- Remove any identities associated with employee-owned devices
- Revoke session tokens from APIs, your Identity Provider (IdP), or Single-Sign On (SSO) provider
- Remove the employee from any access control security groups
- Review remote access software and VPN credentials to ensure the former employee doesn’t have access to it
Conclusion
Employees that are disgruntled by an upcoming termination pose a significant threat to data security. Their dissatisfaction can motivate them to steal sensitive data and sell it to competitors or threat actors. By carefully managing the offboarding process, auditing employee computer activity, and retaining control over access to sensitive data you can mitigate these offboarding risks.
In today’s privacy-conscious world employers need to monitor employees in a way that is transparent, minimally invasive, and respectful of employee privacy. Read this white paper to learn the best practices for monitoring employees in the workplace.
Get the FREE white paper now
Business & Finance Articles on Business 2 Community
(65)