Computer storage has come a long way since the days of punch cards, and alongside it has come advances in cyber protection. Since the first magnetic hard drives of the 1950s, hackers have wanted to gain access to business storage, often with great success. Today protecting your company from hackers is a matter of routine, but is there a way to do better.
The first computer virus came around in 1971 as an experiment, and while it was never unleashed it sparked the beginning of cybersecurity. Once it was demonstrated that a threat was possible to computer memory, cybersecurity professionals got to work figuring out how to defend against those threats.
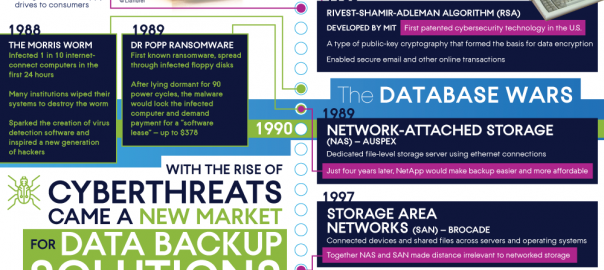
The Morris Worm came around in 1988 followed by the first ransomware in 1989, which sparked a new wave of data backup solutions. These were threats that could wipe out all the information on a business’ hard drive, leaving them with nothing, so backing that data up at an offsite location was often the best defense. This storage went through a number of iterations, from on-site to attached to shared to finally offsite thanks to the internet.
Today’s cyber threats are varied, and cybersecurity professionals have their work cut out for them. One of the biggest threats we face today is Deepfakes, which can call into question the legitimacy of just about any piece of information out there. Determining legitimacy is going to be the next frontier of cybersecurity.
Whenever new tech is developed it brings along with it new risks. Are we prepared to face the next wave of cybersecurity threats that businesses face? AI and machine learning are already giving businesses great actionable intelligence, but the more data that is stored in networks, the more opportunities there are for data breaches. Learn more about the evolution of cyber protection from the infographic below.
![The Evolution of Cyber Protection [Infographic] The Evolution of Cyber Protection [Infographic]](https://www.onlinesalesguidetip.com/wp-content/uploads/2020/04/The-Evolution-of-Cyber-Protection-Infographic.png)
Infographic Source: Acronis
Digital & Social Articles on Business 2 Community
(22)